
- Details
- Hits: 2156
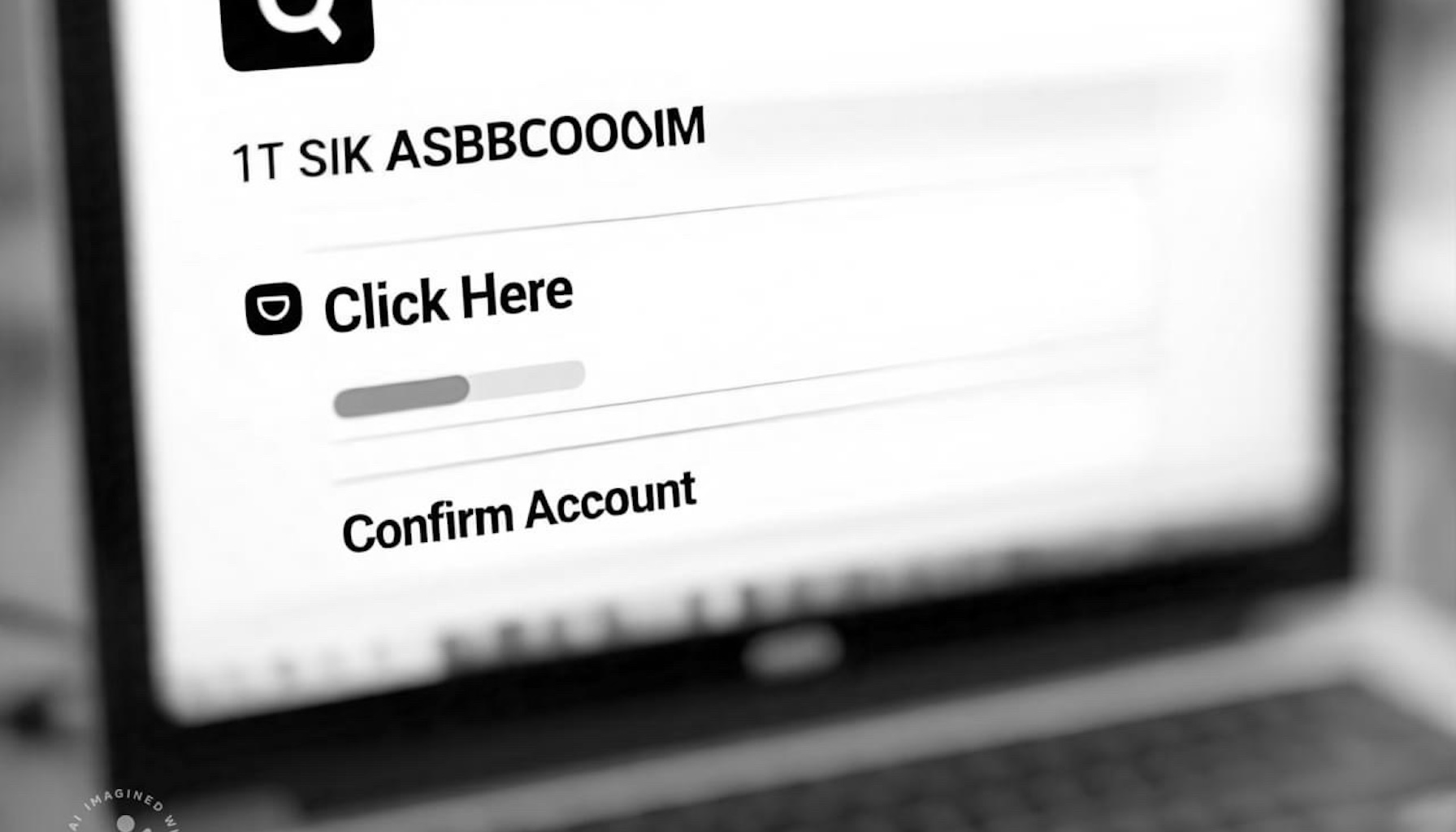
QR codes have become an integral part of our daily lives, offering quick and convenient access to information, payments, and services. From restaurant menus to digital tickets, these pixelated squares have revolutionized how we interact with the world. However, like any technology, QR codes can be exploited by cybercriminals, exposing unsuspecting users to a range of risks. Understanding these dangers and adopting safe practices can help you avoid falling victim to malicious QR codes.
Read more: What You Need to Know About the Hidden Dangers of QR Codes and How to Stay Safe
- Details
- Hits: 1029
Phishing, a cybercrime that tricks individuals into revealing sensitive information, continues to evolve with increasing sophistication. While phishing was once synonymous with suspicious emails, today’s attackers exploit legitimate-looking online services to target unsuspecting users. Free tools like password generators, document converters, and similar platforms have become prime vectors for these schemes.
This article explores how phishing operates through these seemingly harmless tools, the risks they pose, and practical steps users can take to protect themselves.
Read more: Understanding Phishing: The Hidden Risks of Free Online Services

- Details
- Hits: 1306
Artificial Intelligence (AI) is making waves across many industries, but one area where it’s proving to be a game-changer is cybersecurity. With the rise in digital threats, AI is stepping up to help organizations better protect their data and systems. In this article, we’ll look at how AI is transforming cybersecurity, why it’s becoming essential, and what this means for the future of digital security.
Read more: AI in Cybersecurity: How Artificial Intelligence is Shaping the Future of Digital Defense

- Details
- Hits: 1370
As the fall season approaches, organizations must not only prepare for colder weather but also fortify their digital infrastructure. Cybersecurity threats continue to evolve, and hackers often take advantage of vulnerabilities during transitions, such as season changes when companies may be less vigilant. Fall presents an opportunity for leaders, management, supervisors, and cybersecurity teams to refresh their cyber hygiene practices and ensure the organization remains resilient against cyberattacks.

- Details
- Hits: 1522
Artificial intelligence (AI) has become an integral part of our daily lives, influencing decisions from medical diagnoses to driving directions. While AI offers immense potential for innovation and efficiency, it also raises critical questions about trust, transparency, and reliability. To understand how much we can trust AI, it is essential to delve into the sources of its information, the accuracy of its outputs, the prevalence of fabricated stories, the potential for human manipulation, its impact on human evolution, the environmental impact of its energy consumption, and whether its popularity is driven by human traits like laziness, greed, and the desire for quick success.

- Details
- Hits: 865
For many, the internet connection seems to magically appear through a single box provided by their internet service provider (ISP). This box, often a modem-router combo, fulfills two crucial functions: connecting you to the wider internet and creating your home Wi-Fi network. But when it comes to security and privacy, relying solely on an ISP-provided modem-router might leave your digital life exposed. This is where a private security gateway (firewall) steps in, offering a more robust defense against online threats.
Read more: Fortress at the Front Door: Why a Private Security Gateway Beats Your ISP's Modem-Router
